Table of Contents
Introduction
To more secure the user logins we can enable two-factor(2FA) authentication to your POD.
In this article, we will discuss how to use Microsoft NPS acting as our RADIUS Server and we use windows authentication only as of the first authentication
Most of the production use cases will use a third-party radius server which provides a response/challenge to be entered for the first authentication.
Assuming we have already had a Windows server deployed in Azure and all required networking (vNET peering, NSG rules and etc) configured
Prerequisites
- Windows Server Operating System
- NPS Role
- Gateway DMZ IP’s
Install NPS Role
- Launch Server Manager
- Click on Manage and Select Roles & Features

- Click on Next and select Role-based or feature-based installation
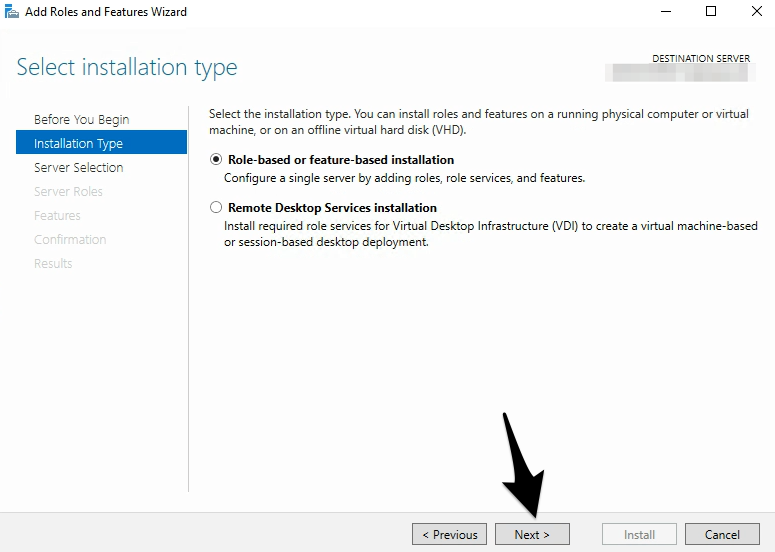
- Click Next (With default values)
- In Roles Section, Select Network Policy and Access Services and click on Add Features, and click Next

- Click Next (With default values)
- Select Next on Network Policy and Access Services Section

- Click on Install and wait till finish
- Once the NPS role installed, we can see it the Server Manager
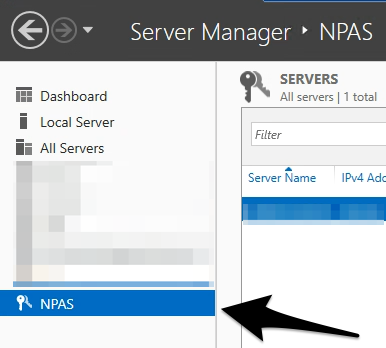
Configure NPS as a Radius
- Select NPAS and right-click on the server’s name and select Network Policy Server
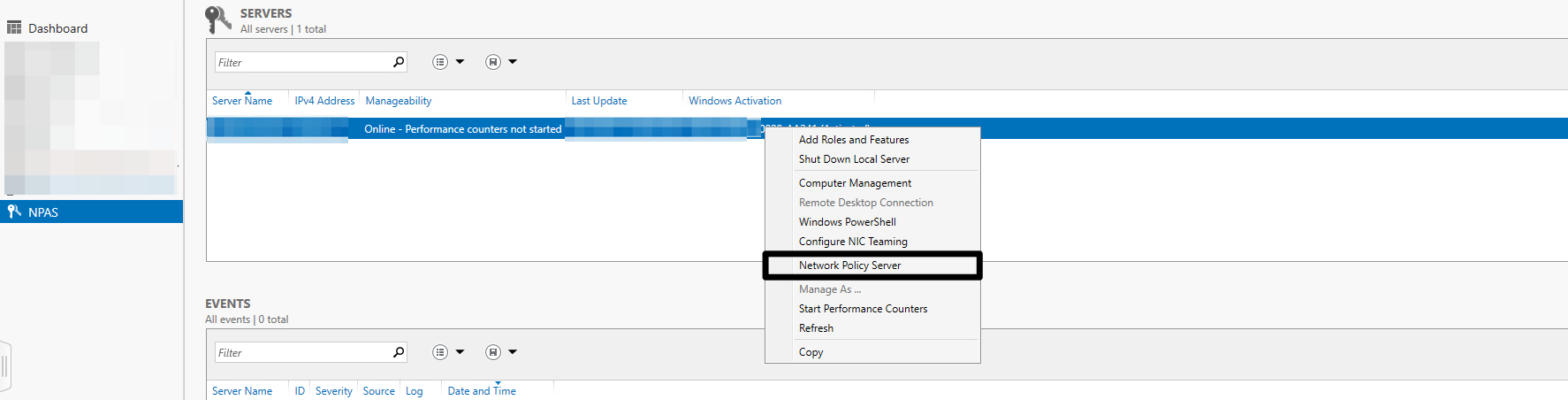
- You will see the below screen

- Note down the DMZ IP’s of UAG ( vNET –> overview –> search as “dmz”
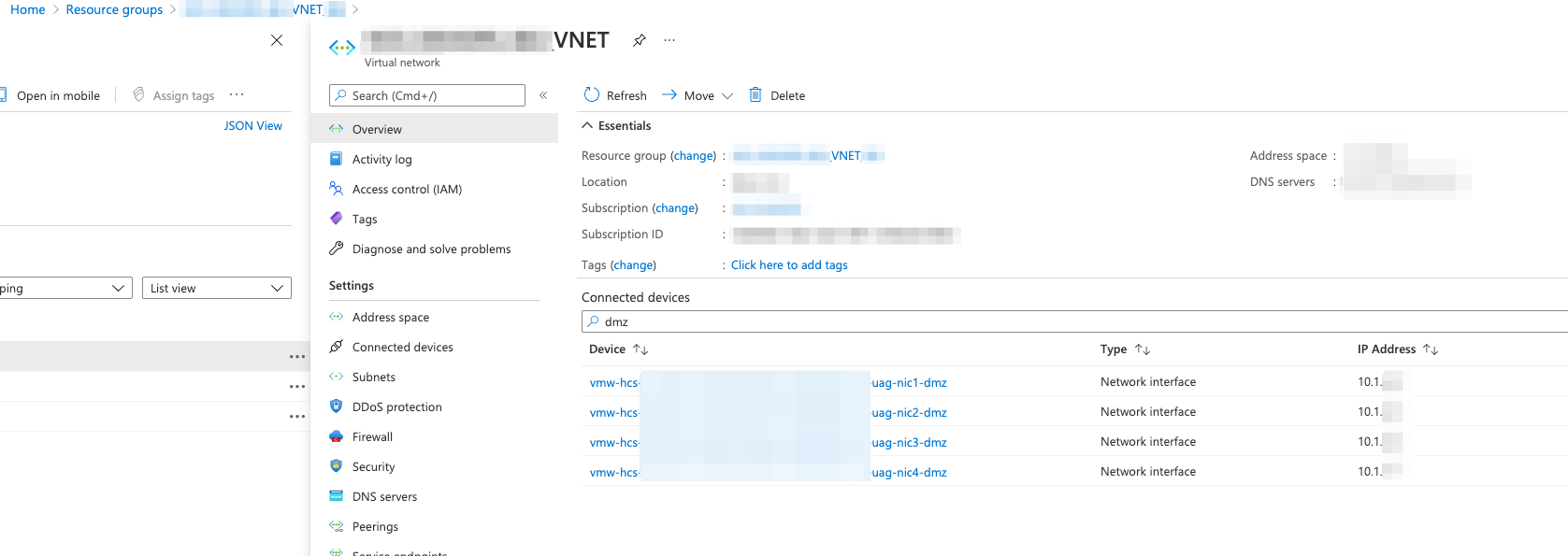
- In RADIUS Clients provide the DMZ IP’s (Provide all 4 of them, so that after tenant upgrade it won’t affect logins)

- Click on Policies and select Network Policies

- Right-click on Network Policies and Select New
- Provide a Policy Name, other leave as defaults then clicks Next
- Select User Groups, Provide the User group who log in through appblast portal
- In next screen, Select Access Granted
- Select the required Configure Authentication Methods and click on Finish
In my setup created policy as like below

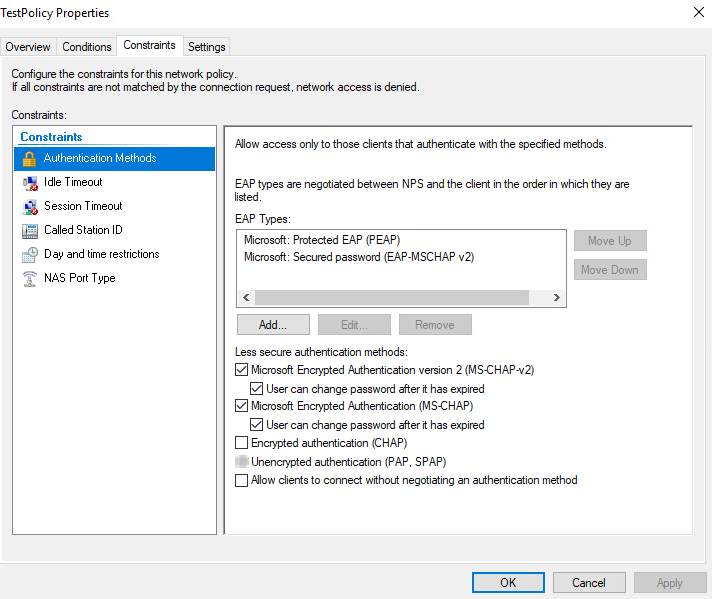
Note: Please use a RADIUS server which gives challenge , here am trying to show how to configure and this use Windows authentication only
Configure RADIUS on Horizon
- Log in to the Horizon admin console
- From Settings –> Click on Capacity
- Select the POD Name –> Click on EDIT
- Move to Gateway Settings
- Move the toggle next to Enable 2 Factor Authentication

- Enter details (RADIUS Server IP, Shared secret)
–> Authentication Port – 1812
–> Accounting Port – 0 (keep it as 0 if Accounting is not configured else RADIUS login will wait 60+ seconds and at times it fails)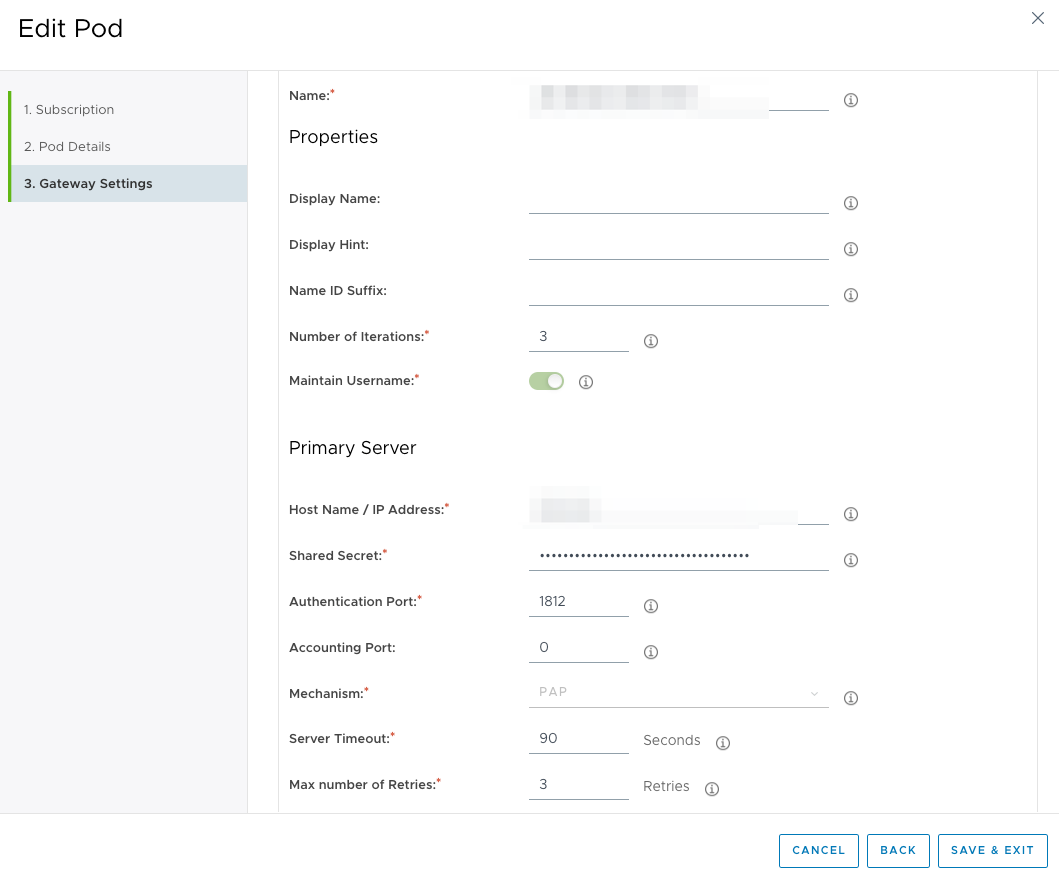
Please do the above config on a maintenance window else there is a high chance of users existing sessions will get disconnect
![Horizon Cloud on Azure – Introduction [Part-1]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-intro-feature-image-1024x624.png)
![Horizon Cloud on Azure – POD Deployment & Troubleshooting [Part-2]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-POD-deployment-feature-image-1024x636.png)