Once the POD is created the next step is to add the pod to Domain so that an administrator can start leveraging the solution.
Pre-Requisites for Domain Bind:
- vNet created during deployment have access to the company active directory (make it possible using either peering or Express route if domain controllers are on-prem)
- Check the below VMware public article for Domain bind Port requirements
Ports and Protocols Requirements for a Horizon Cloud Pod at the September 2019 Release’s Manifest or Later (vmware.com) - Once required ports are opened by following the above document, an administrator can test networking by deploying a VM in the management subnet. Vmware public documents is very clear for this step
Troubleshooting If You Encounter Pod Deployment or First-Time Domain Bind Issues (vmware.com) - We need a total of 4 service accounts where 2 for Domin bind and another 2 for Domain join
- Once the domain registration is completed, the Domain workflow asks to input a security group name for the Super Admins role on the admin page. so have a security group ready and add the persons who require complete access to the Admin console
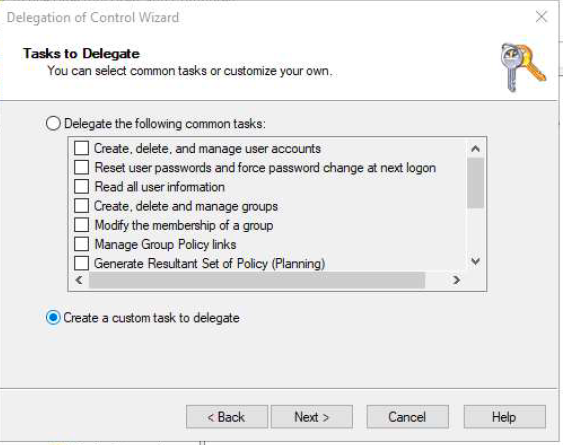
Service account Permissions: –
Domain bind service accounts: –
we need 2 service accounts for Domain bind
1 –> Primary
2 –> Auxiliary ( this will be used when primary domain bind account locked / password expired)
VMware Public documentation – Service Accounts That Horizon Cloud Requires for Its Operations (vmware.com)
Based on my experience, Just create a default domain account with a password never expires is sufficient for a bind account
Domain Join service accounts: –
VMware documentation clearly states that this account requires some specific privileges, so even if we set Full Control for that account it won’t help.
Any Horizon pods in Microsoft Azure are running manifest 2474.0 or later ( Ex: 2474 and 2672 )
| Access | Applies to |
|---|---|
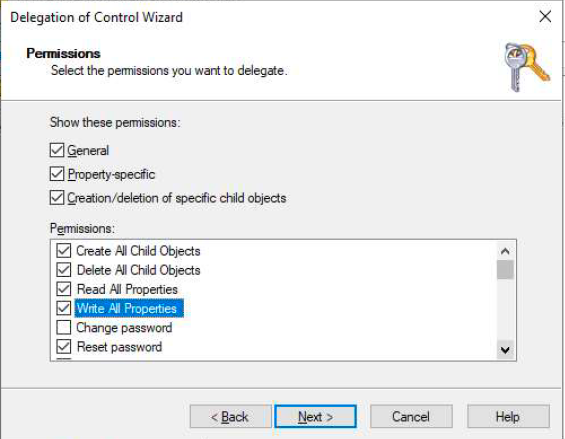
| Read All Properties | This object only |
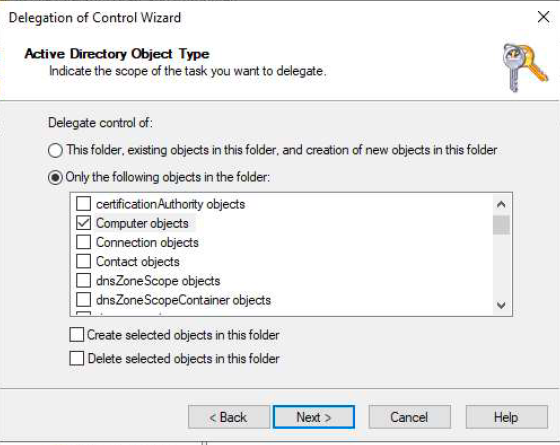
| Create Computer Objects | This object and all descendant objects |
| Delete Computer Objects | This object and all descendant objects |
| Write All Properties | Descendant Computer objects |
| Reset Password | Descendant Computer objects |
Any Horizon pods in Microsoft Azure that are running a manifest prior to 2474.0 ( Ex: 2298 , 1976 , 1763 and 1600 etc)
| Access | Applies to |
|---|---|
| List Contents | This object and all descendant objects |
| Read All Properties | This object and all descendant objects |
| Create Computer Objects | This object and all descendant objects |
| Delete Computer Objects | This object and all descendant objects |
| Write All Properties | All descendant objects |
| Read Permissions | This object and all descendant objects |
| Reset Password | Descendant Computer objects |
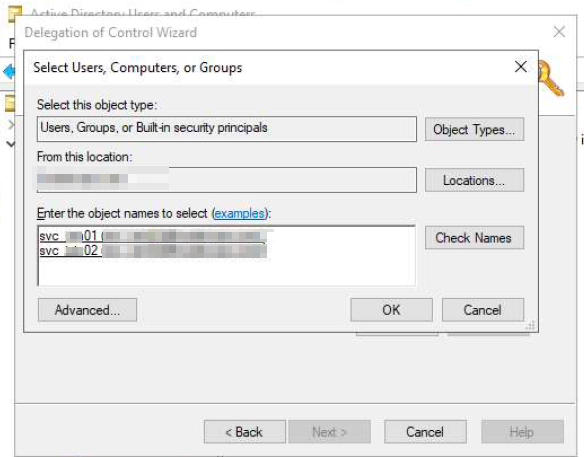
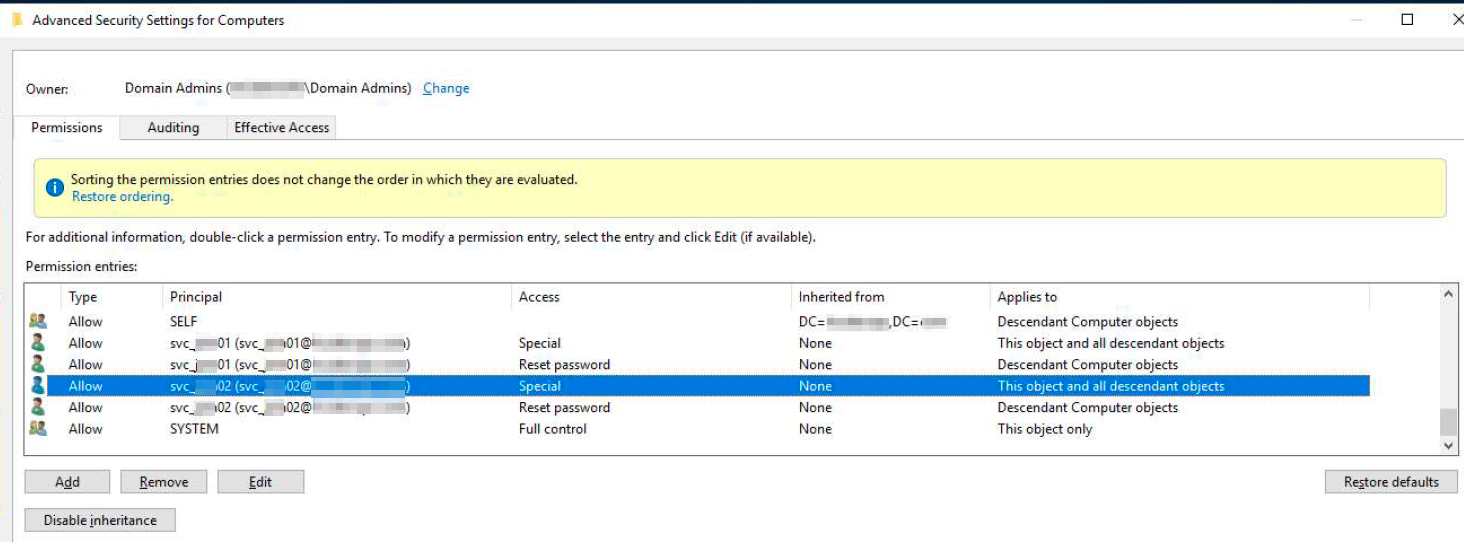
Below series of screenshots may help in providing permissions to 2 of the bind accounts.
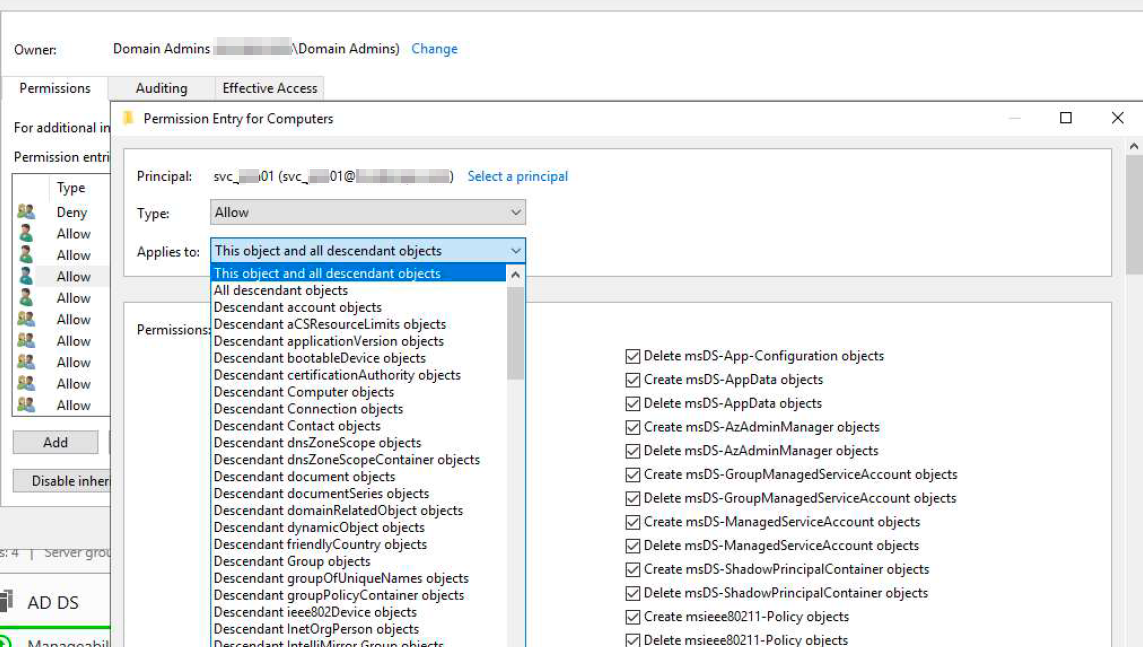
Finally check the affective permissions and it looks below
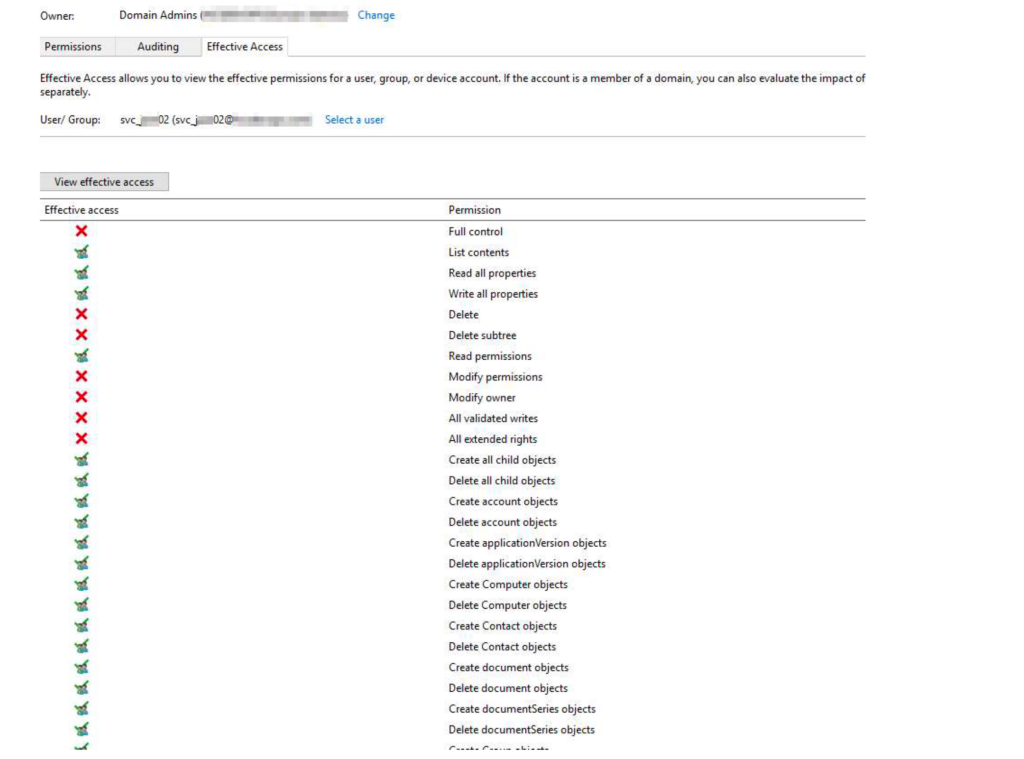
- Now Login to Horizon admin console
- Select Active directory from left side pane else the same you can select from Getting started page
- Click on Register
- Fill in the required details
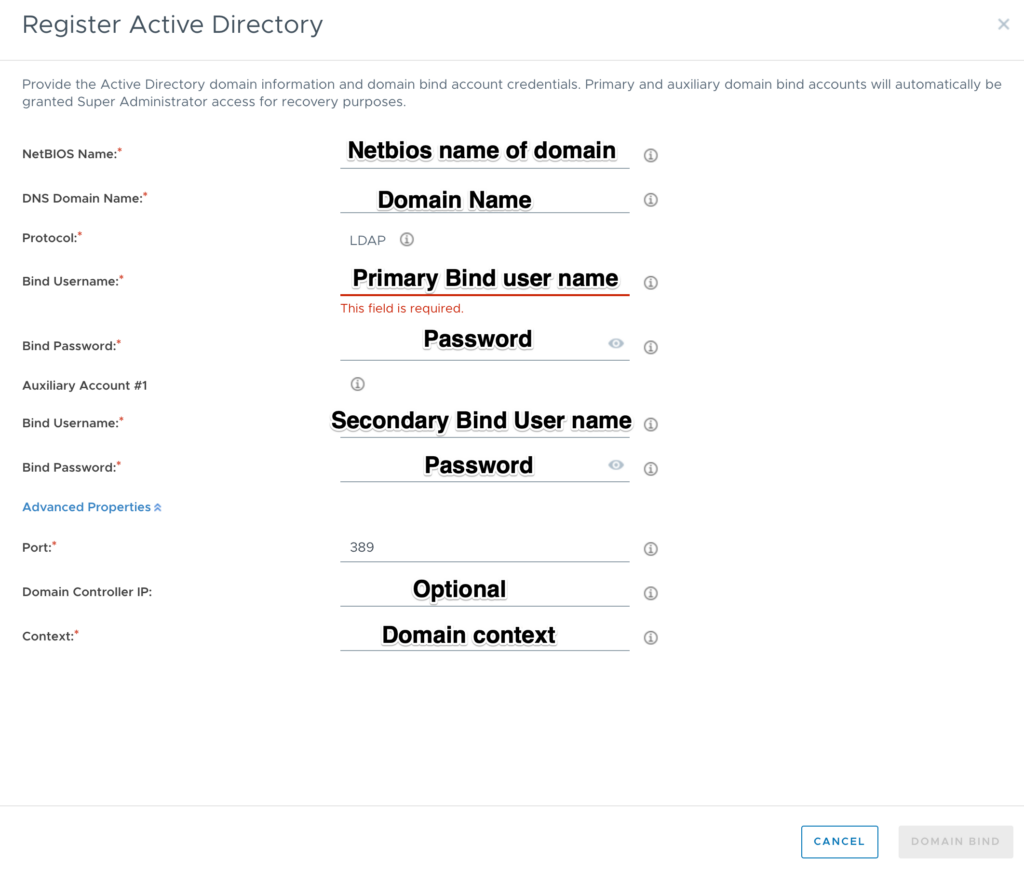
Domain controller IPs are optional, if you don’t provide one then Horizon tries to find the resolvable AD servers from DNS and tries to connect them (here we don’t have visibility to which server it connects to because horizon sorts the IPs based on an algorithm). If IPs are provided, then Horizon tries to connect those servers only to bind the POD
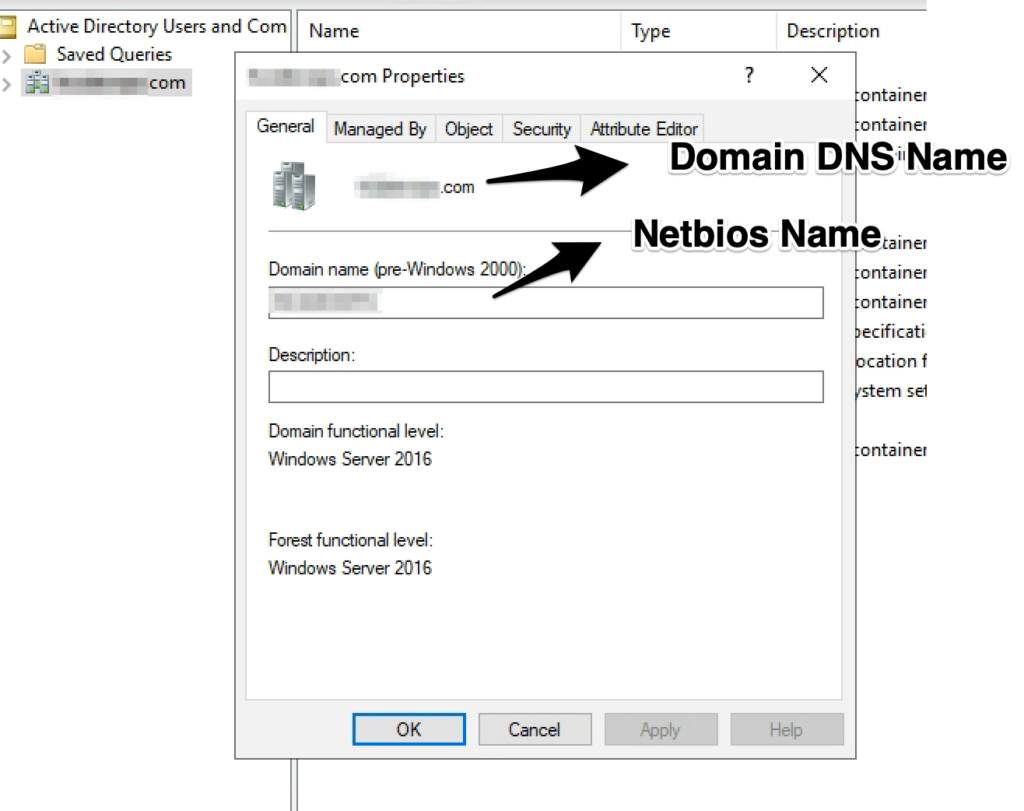
The below screenshot helps to find NetBIOS & DNS domain names
on a successful domain bind, the Active directory workflow goes to another screen where it asks to enter DNS details & Domain join account details.
After Domain join account validation completed, on the next screen it will ask for super administrator group details and Save
By here Active directory binding to the first pod is completed
Subsequent PODs deployments under the same customer account will automatically bind to AD using First domain bind details so that no admin intervention is required.
Common issues while Domain binding:
- Kerberos port is not allowed on Port 88 on both TCP & UDP from POD Manager VM’s
- Global catalog port 3268 is not allowed on GC AD servers from POD Manager VM’s
- Incorrect NetBIOS name
- Domain join account not having the required privileges




![Horizon Cloud on Azure – Introduction [Part-1]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-intro-feature-image-1024x624.png)
![Horizon Cloud on Azure – POD Deployment & Troubleshooting [Part-2]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-POD-deployment-feature-image-1024x636.png)