Table of Contents
Introduction
From UAG 3.8 onwards , VMware supports third party IDP’s authentication using SAML.
In this article , we will try to learn how to integrate Azure Multi-Factor Authentication (MFA) with VMware Unified Access Gateway
Prerequisites
- VMware UAG (minimum version 3.8)
- Azure AD Subscription
- MFA feature included Azure license
- Azure AD connect to synchronise on-primse users & groups from Active Directory
- Existing UAG URL
- Global Administrator account in Azure AD
Azure side configuration
- Login to the Azure Portal (an user having Global admin privilages)
- Search for Azure Active Directory & Click on it
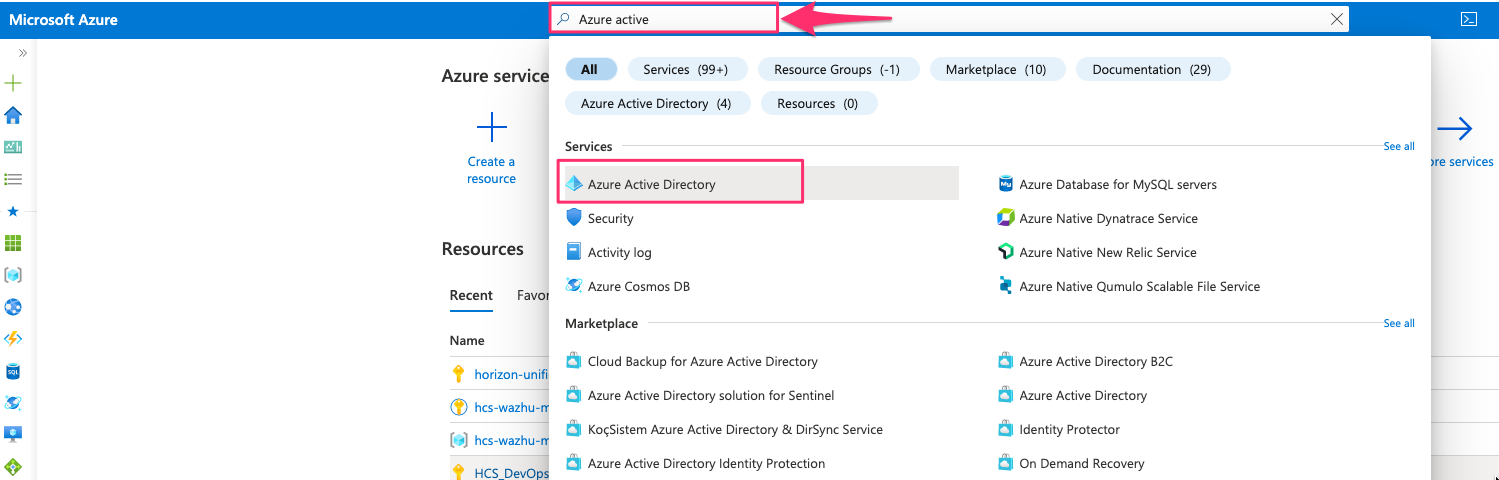
- Select Enterprise applications – For this case I have Azure AD Premium P2 license
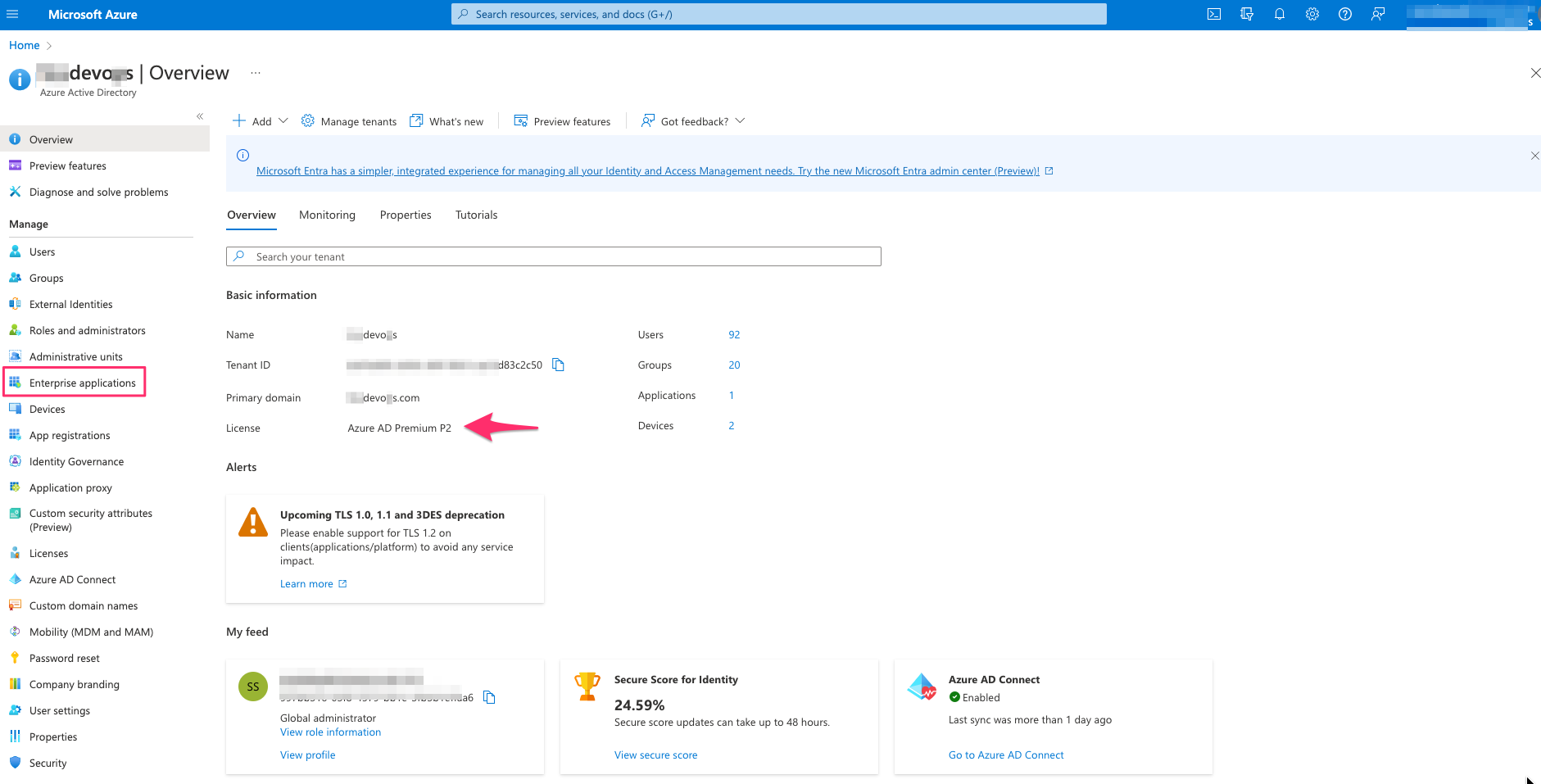
- From All applications – select New application
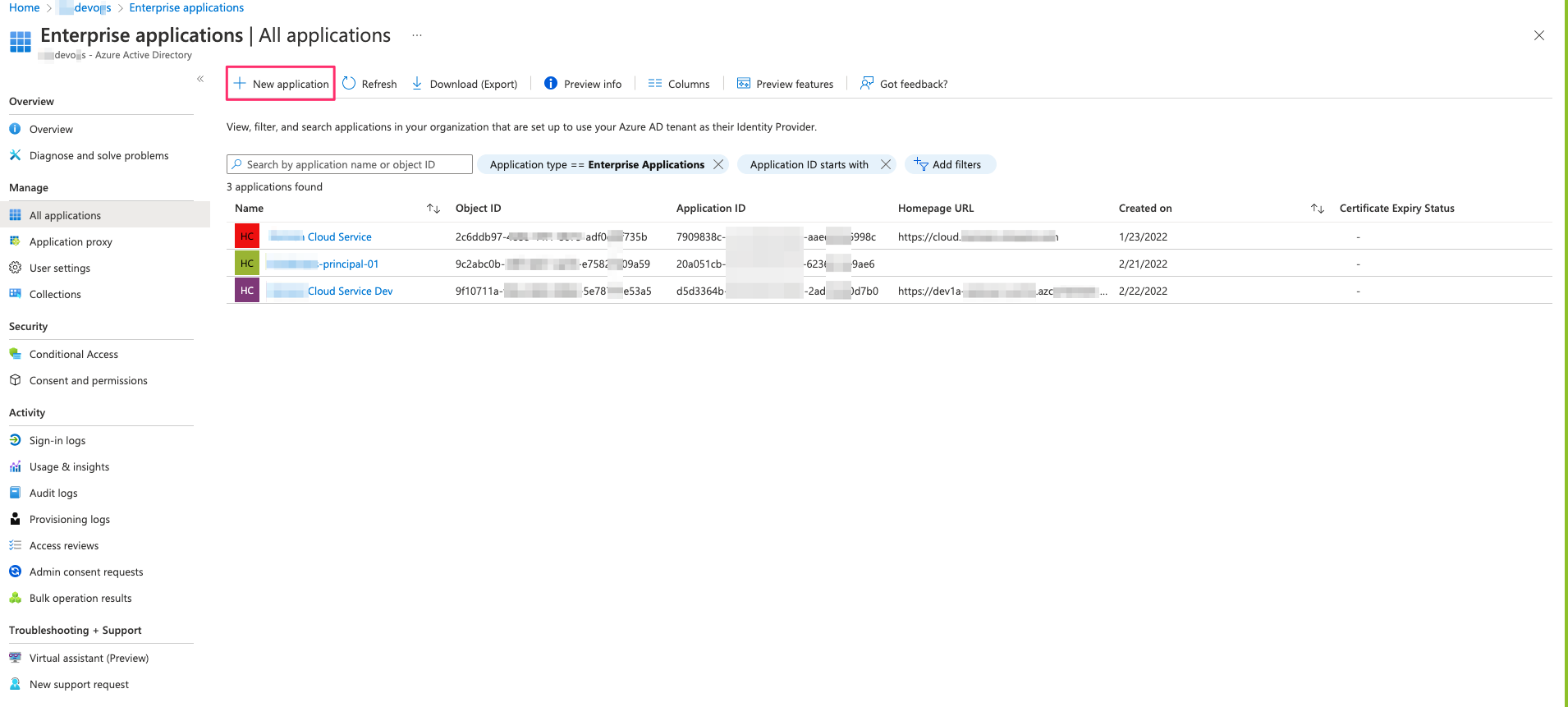
- Search for VMware Horizon and Select VMware Horizon – Unified Access Gateway
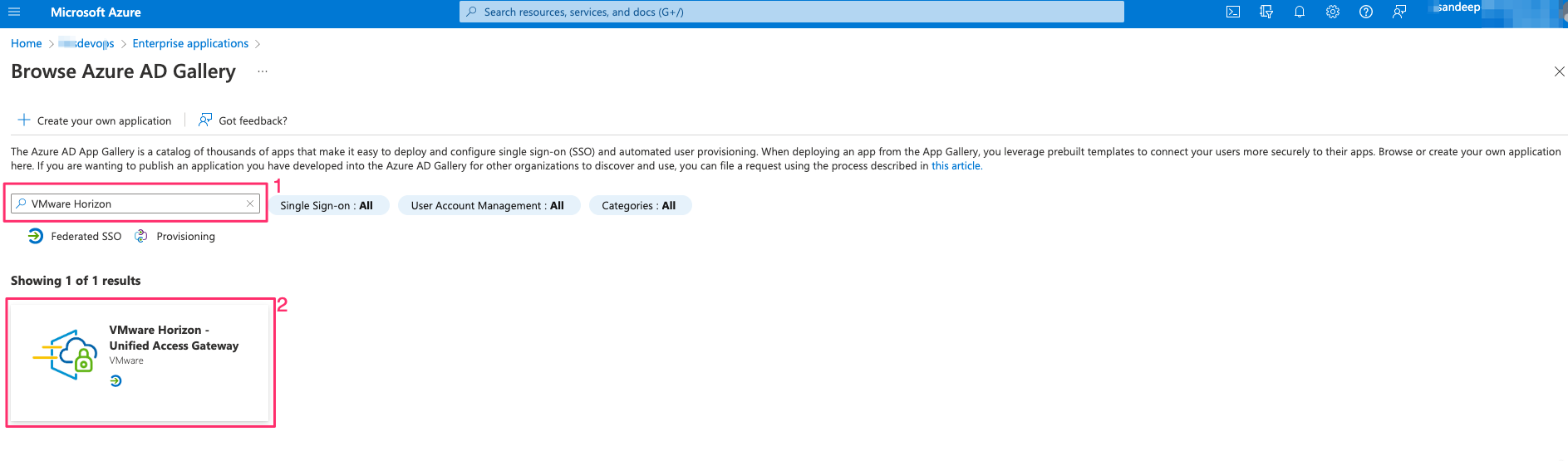
- Click on Create
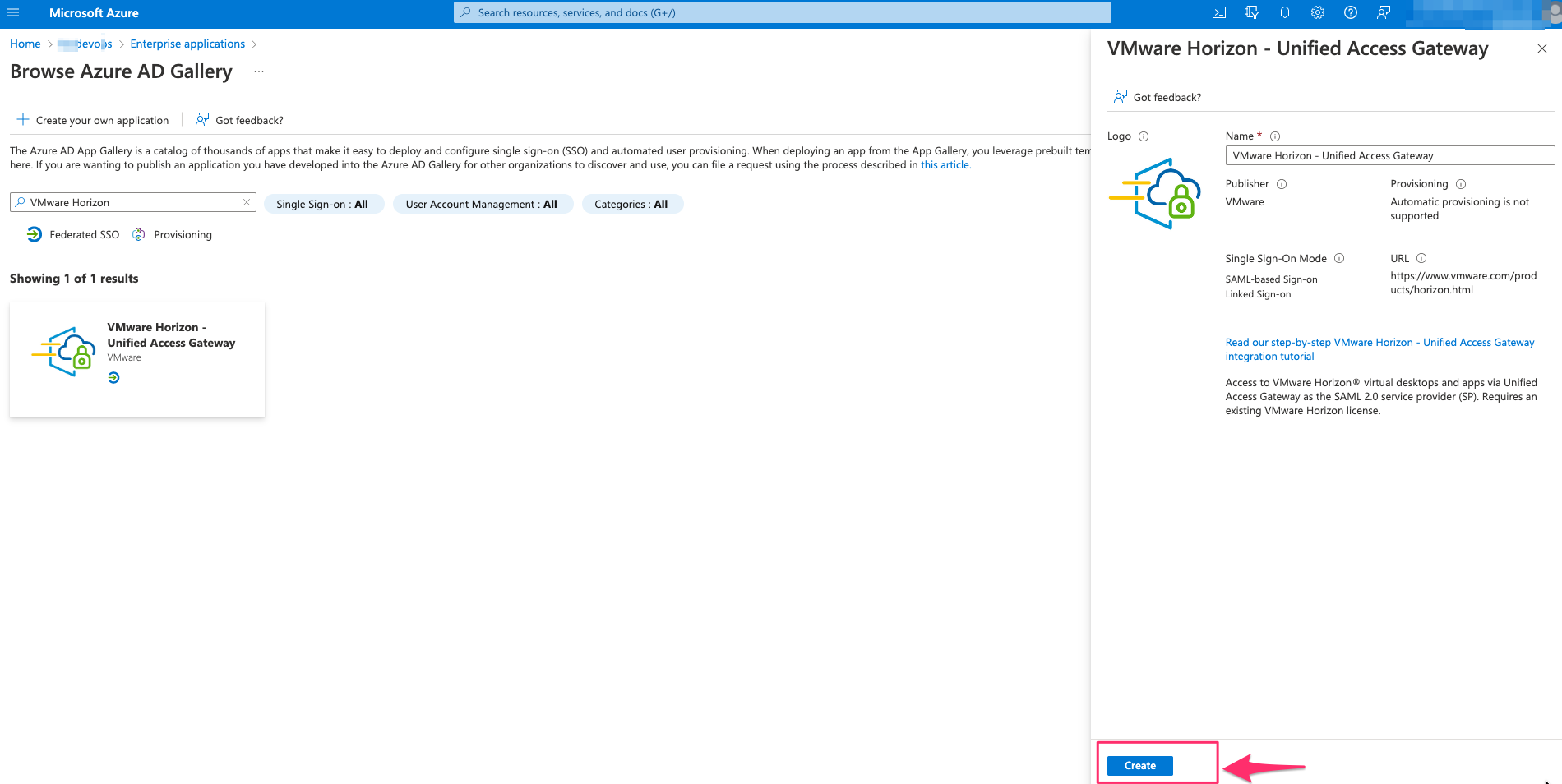
- Wait till the application is added to the portal
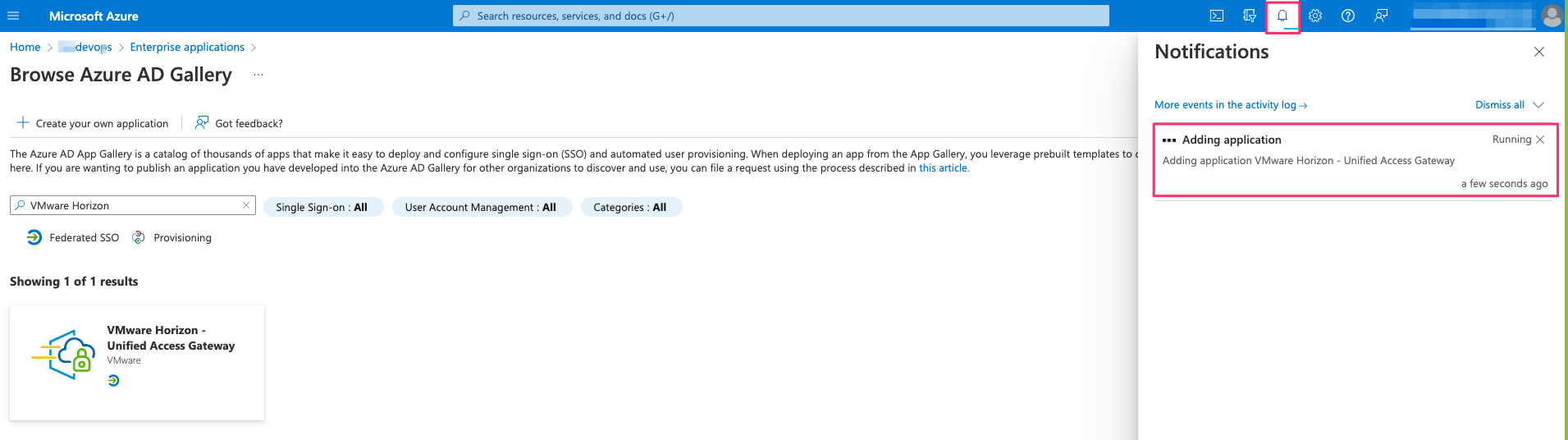

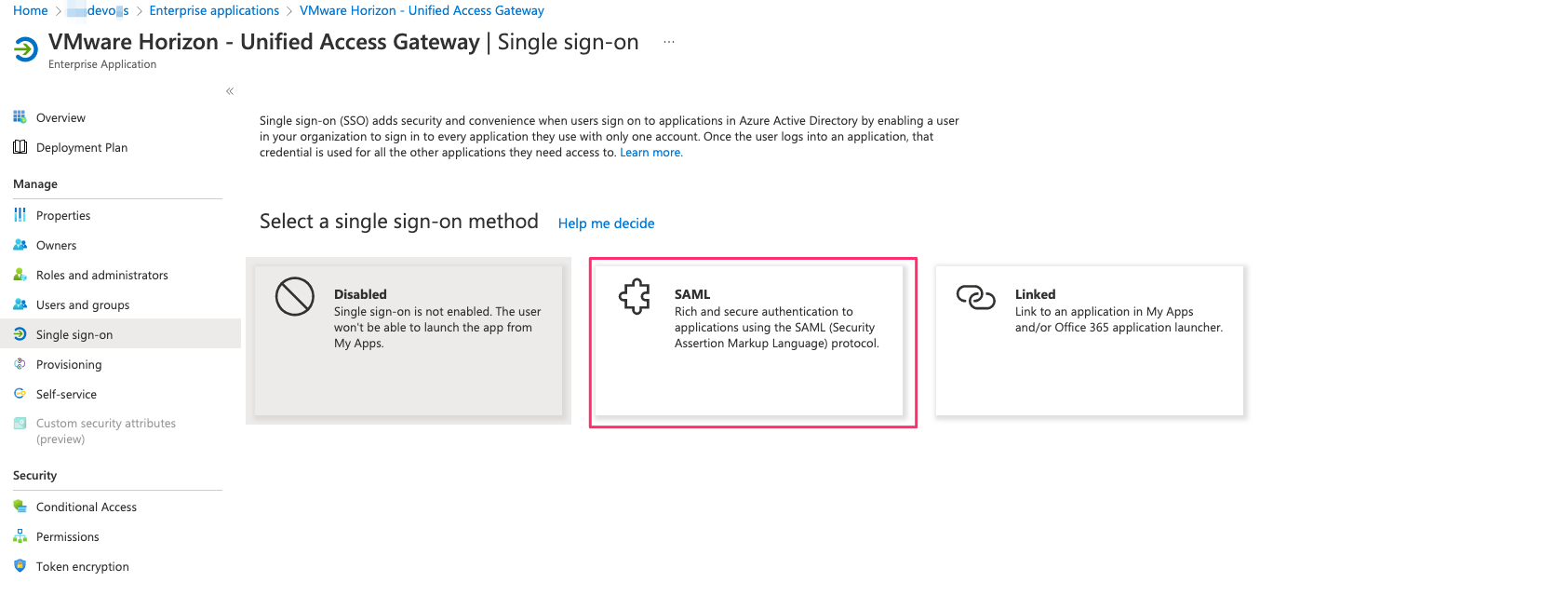
- Click on VMware Horizon – Unified Access Gateway and once you are inside the application , Click on Single sign-on

- Select SAML
- Edit Basic SAML Configuration & Enter the details as below -> Save
Identifier (Entity ID) –> https://<UAG FQDN>/portal
Reply URL (Assertion Consumer Service URL) –> https://<UAG FQDN>/portal/samlsso
Sign on URL (Optional) –> https://<UAG FQDN>/portal/samlsso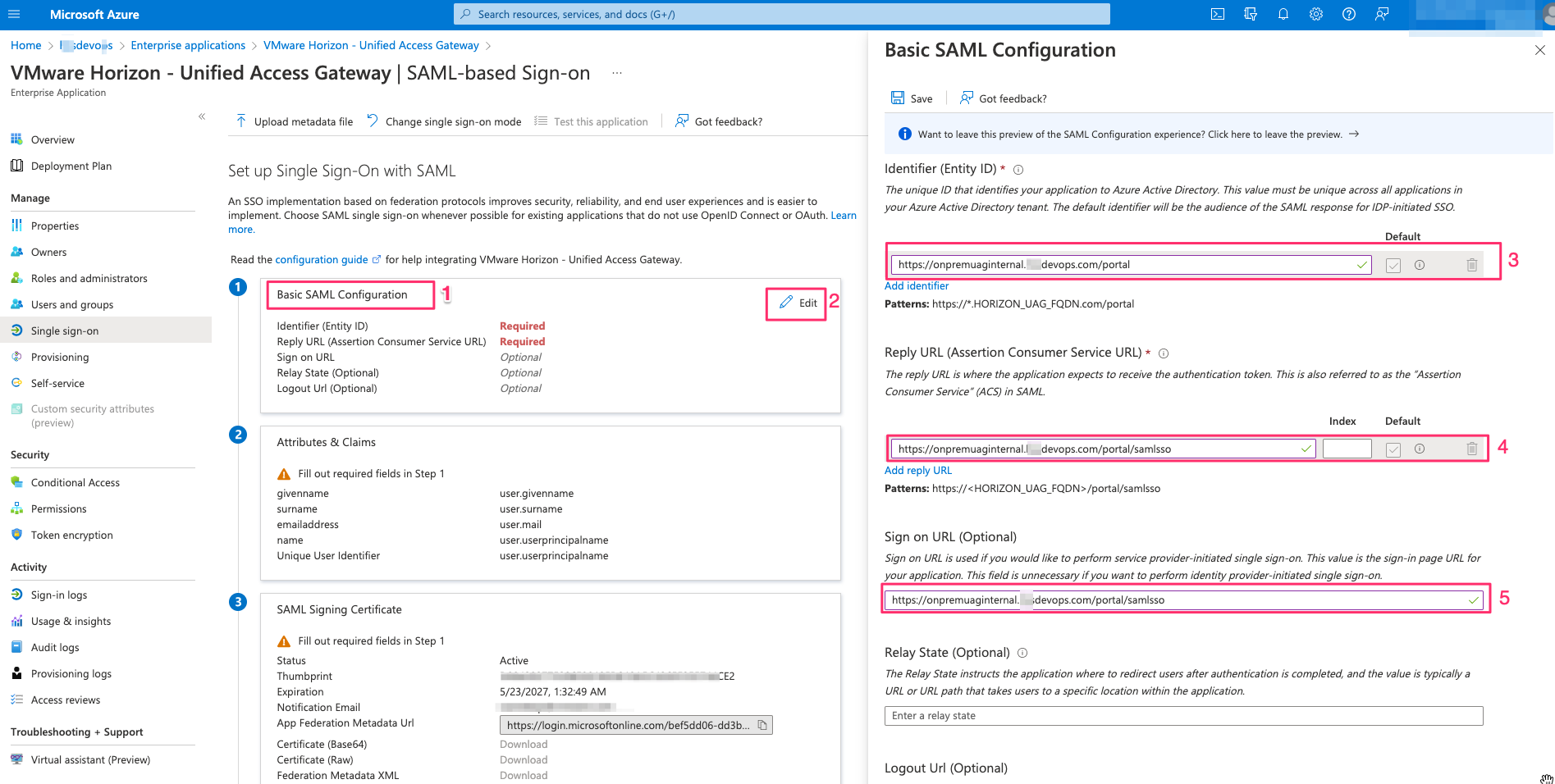
- Now download the Federation Metadata XML
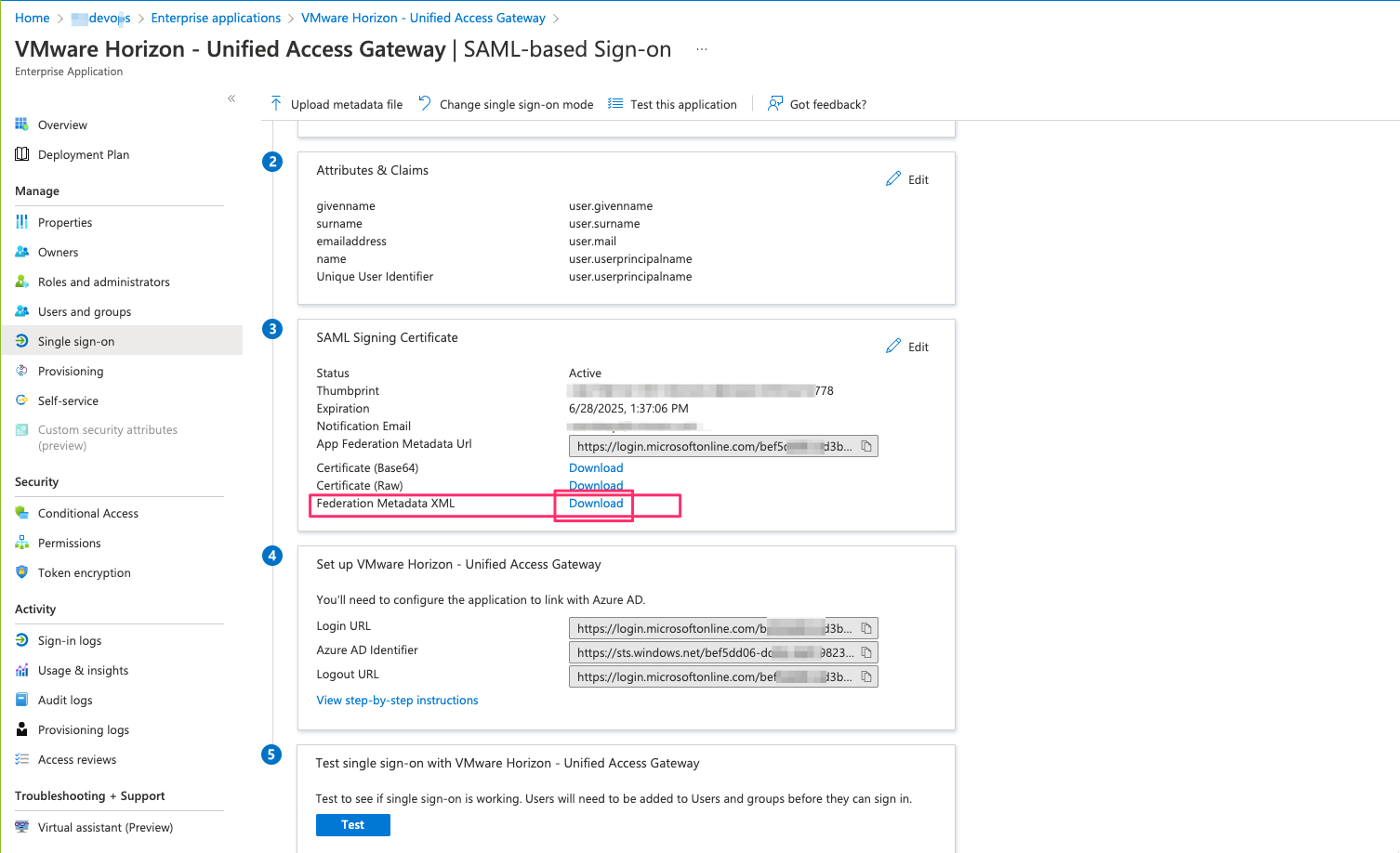
UAG configuration
- Login to UAG as admin using URL –> https://<uag fqdn >:9443
- click on configure manually
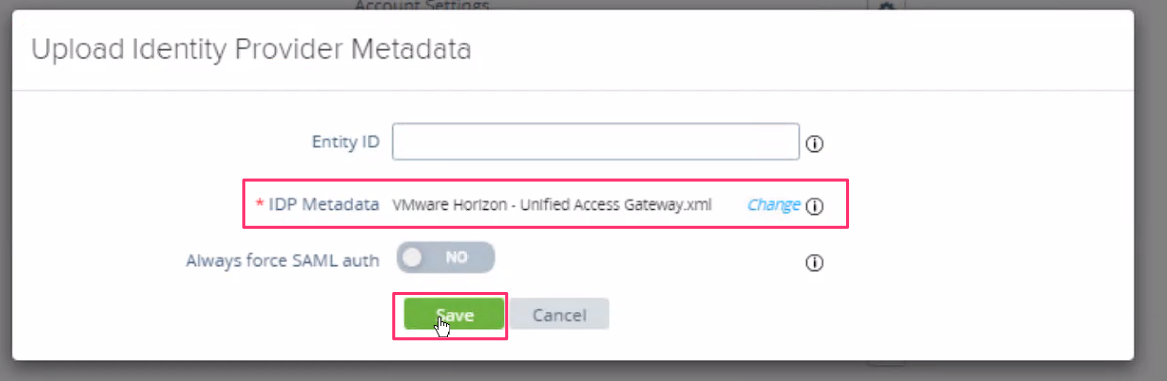
- In the Advanced settings section , click on settings icon button of Upload identity Provider Metadata
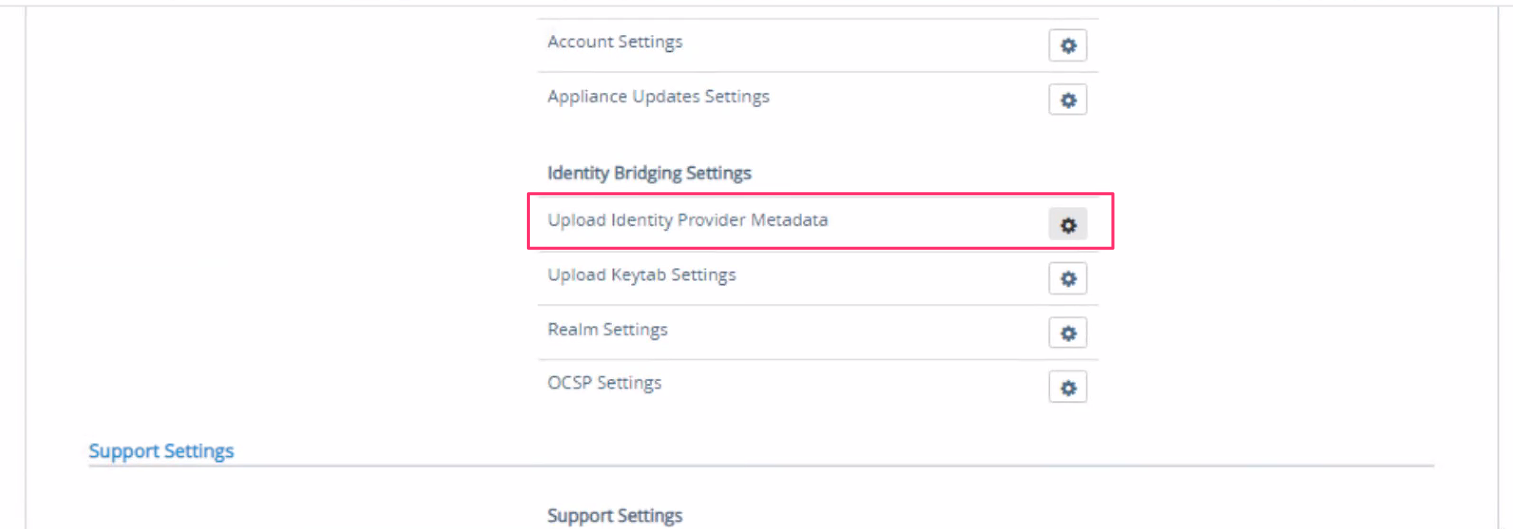
- Click on select which is next to IDP Metadata
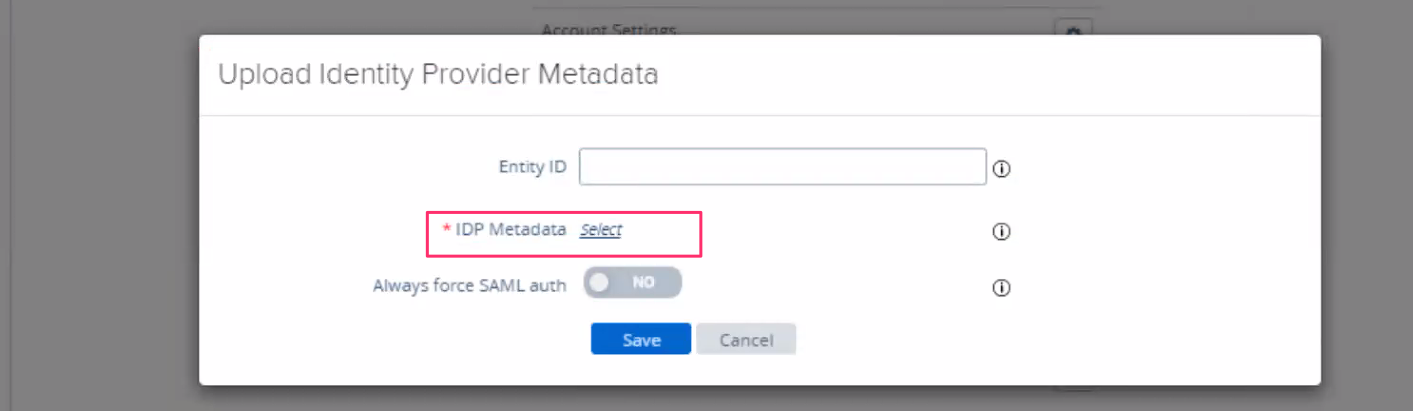
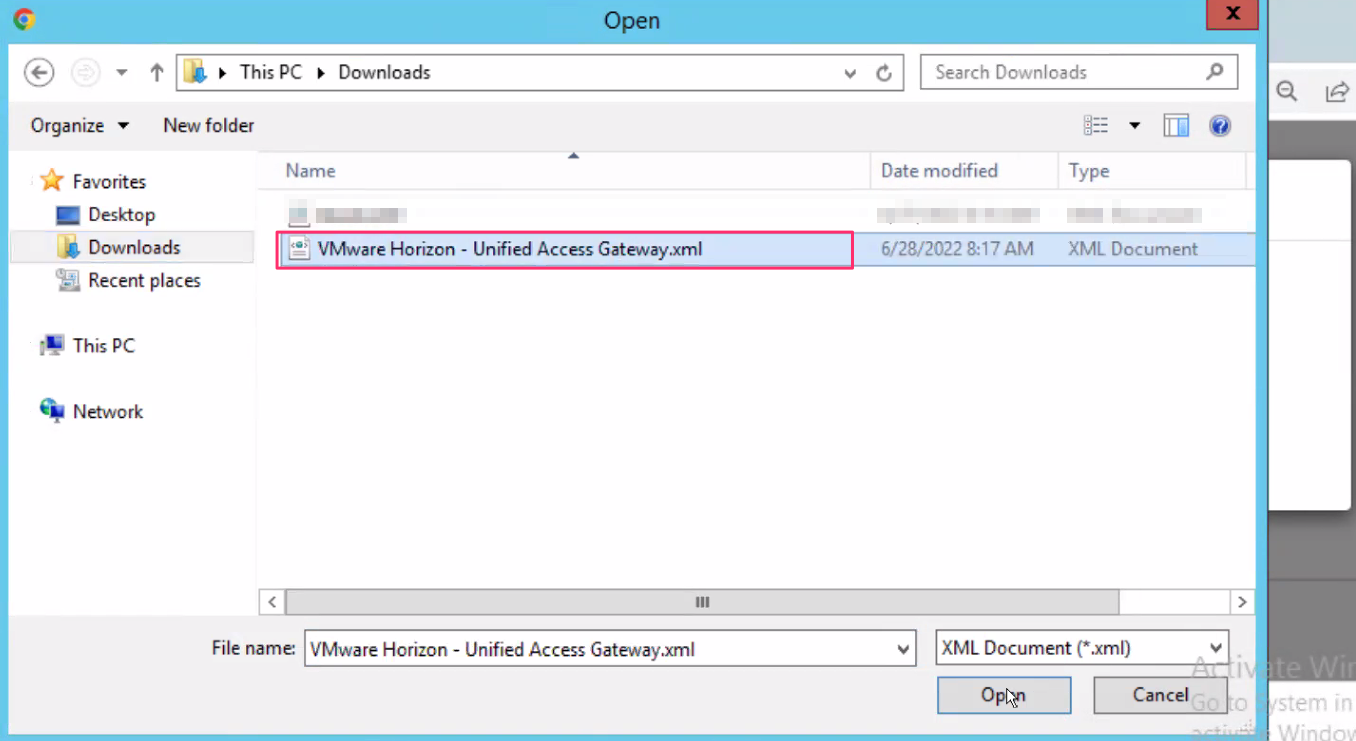
- Upload the downloaded Federation Metadata XML file from azure side configuration and click on Save
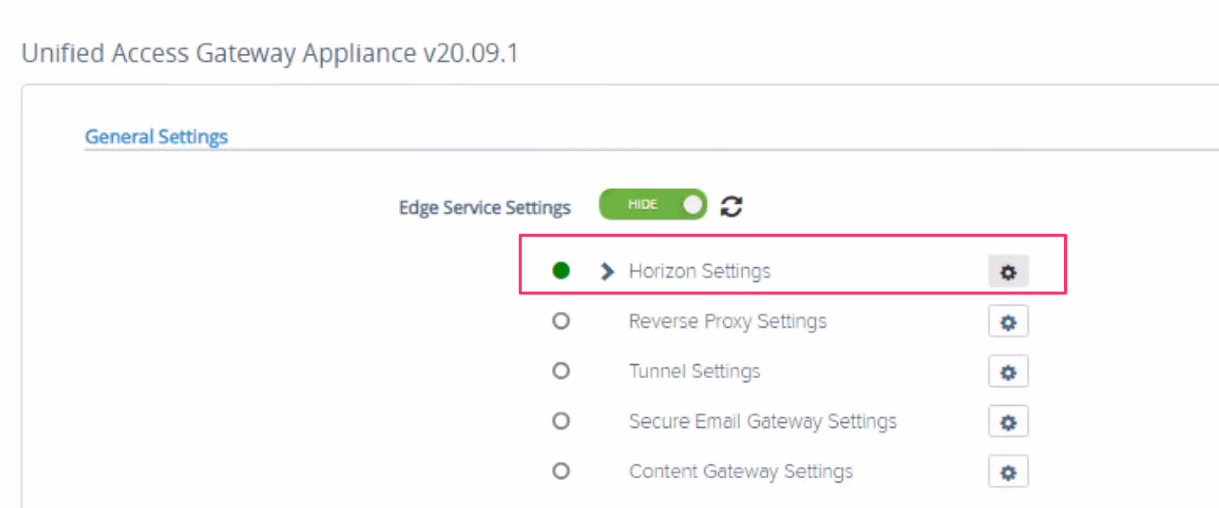
- Under General settings section , click on settings icon button of Horizon Settings
- From Auth Methods drop down , select SAML
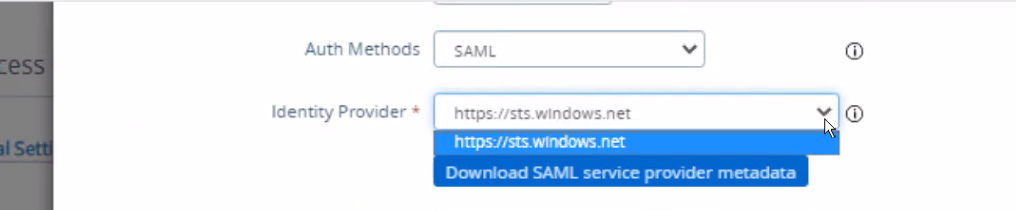
We can see Identity Provider is chosen as Azure MFA (https://sts.windows.net)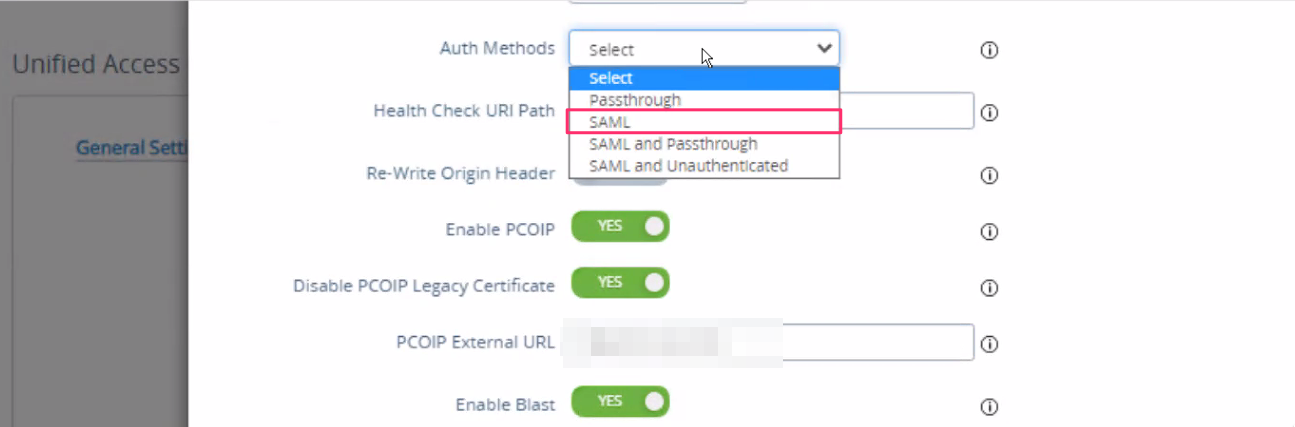
![Horizon Cloud on Azure – Introduction [Part-1]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-intro-feature-image-1024x624.png)
![Horizon Cloud on Azure – POD Deployment & Troubleshooting [Part-2]](https://thecloudwiki.com/wp-content/uploads/2021/04/HZC-POD-deployment-feature-image-1024x636.png)