Due to the readability and ease of updating in future dividing the Horizon Cloud next-gen deployment in multiple posts
We can classify the requirements based on the below
Without completing the pre-requisites it’s not advisable to start with the deployment since the deployment may fail at any stage
In this post , we will discuss about Azure Subscription pre-requisites in-detail
Table of Contents
Azure Subscription :
Valid Azure Subscription
- We need have a valid Azure Subscription in one of Azure Commercial or Azure Gov environments
- At the time of writing this post Horizon Cloud on Azure next-gen supports below Azure regions for the deployment
“westus”,”westus2″,”westus3″,”centralus”,”eastus”,”eastus2″,”northcentralus”,”southcentralus”,”westcentralus”,”canadacentral”,”canadaeast”,”brazilsouth”,”northeurope”,”westeurope”,”uksouth”,”ukwest”,”francecentral”, “francesouth”,”switzerlandnorth”,”switzerlandwest”,”germanynorth”,”germanywestcentral”,”norwaywest”,”norwayeast”,”eastasia”,”southeastasia”,”japaneast”,”japanwest”,”australiaeast”,”australiasoutheast”,”australiacentral”,”australiacentral2″,”centralindia”,”southindia”,”westindia”,”koreacentral”,”koreasouth”,”uaecentral”,”uaenorth”,”southafricanorth”,”southafricawest”
Service Principal
As everyone know , Service principal is an identity used by applications , services and automation tools to access specific azure resources
With respect to horizon cloud next-gen , Horizon service uses API’s to deploy resources on provided Azure subscription to create & manage resources – and to manage those resources horizon uses these service principals
With 4 service principals horizon next-gen supports 5000 VDI’s on ONE Subscription .
Steps to create a service principal :




Service principal permissions :
To manage the resources in the Azure subscription the service principal needs permissions. By providing contributor role in Azure provides is a simpler way to go with deployment since this built-in role contains all the permissions required for horizon to make API call’s .
But customers concerned about permissions can go with a custom role by providing only required permissions
Note: These custom roles may change with new releases since please keep an eye on this link and update as and when it’s required.
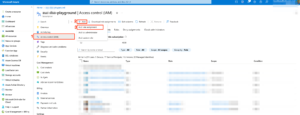
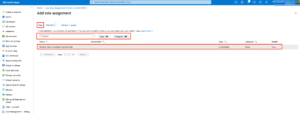
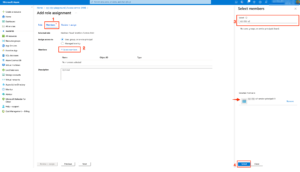
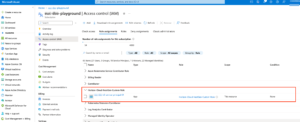
Below is the screenshots on creating customer roles and assign the permissions
Creating custom role

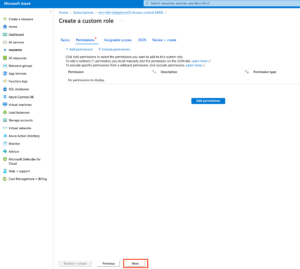
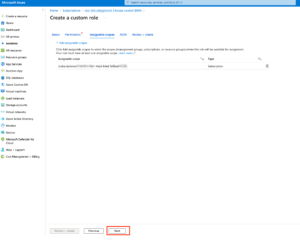

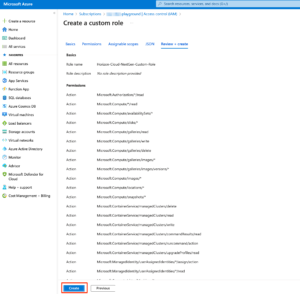
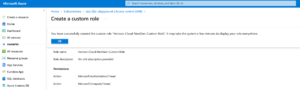
Add role assignment (Custom role + service principal)

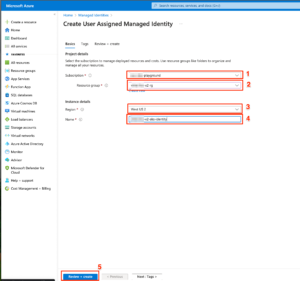
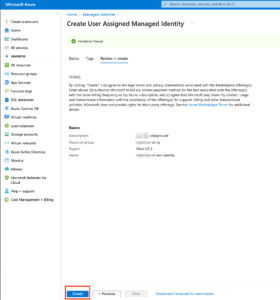
Azure User Managed Identity
There are 2 types managed identities in Azure
1 -> System – assigned
2 -> User – assigned
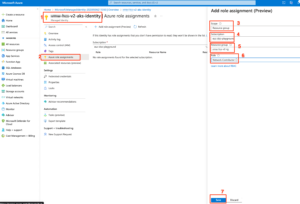
Horizon next-gen edge deployment using an AKS cluster, that requires an Azure User managed identity for RBAC and which requires below 2 roles to be assigned
1 -> Network Contributor role at the management VNet’s resource group scope
2 -> Managed Identity Operator role at the Microsoft Azure subscription scope




Azure policies
We have to make sure that below policies are not enforced on the subscription
1 -> The subscription must allow the creation of resource groups that do not have tags
2 -> Some of the default AKS policies breaks the container creations hence till VMware publishes better not to enforce